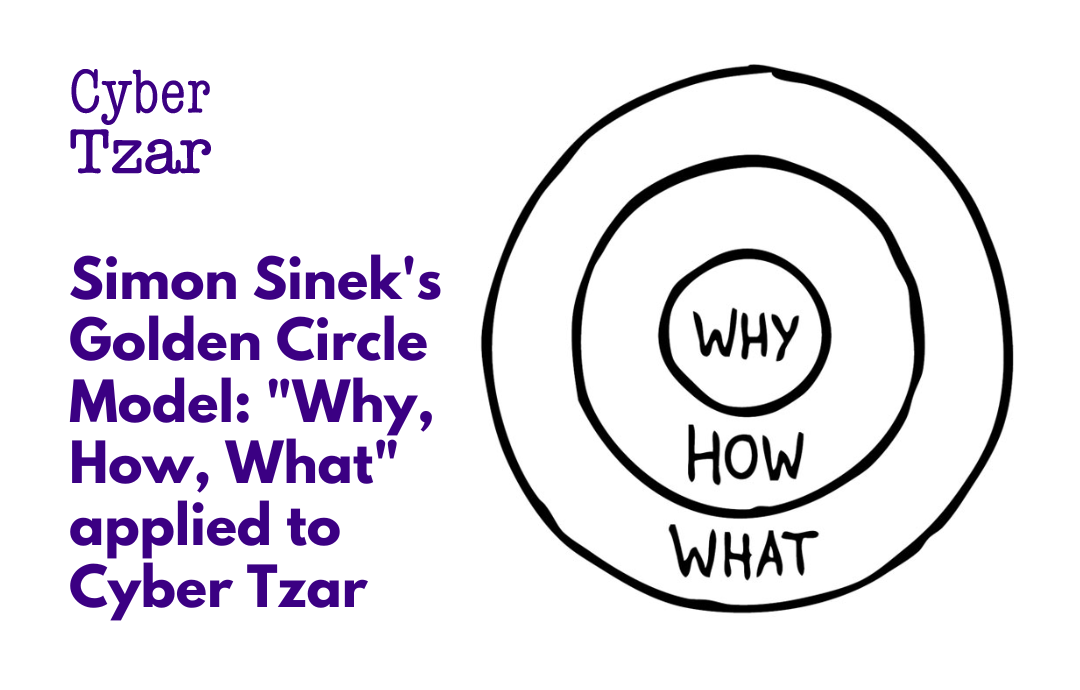
As part of our team’s journey on the NCSC for Startups programme, we were asked to apply Simon Sinek’s Golden Circle Model to Cyber Tzar and our offerings. Although this is a rough attempt it’s what we came up with at the time. obviously, our thinking has moved past this now. But it’s all part of the richness of the evolution of a startup which we think is worth sharing.
An exploration of Simon Sinek’s Golden Circle Model: “Why, How, What” applied to Cyber Tzar
| Use Case | Why | How | What |
|---|---|---|---|
| Credit Score (aka Experian/Equifax)
Existing Example |
To provide a standardized measure of creditworthiness facilitating trust and transparency in financial markets. | Collecting financial data, analyzing it through statistical algorithms, and adhering to legal and ethical guidelines. | Credit reports and scores, credit monitoring, identity theft protection, and financial education resources. |
| Cyber Risk Score | To gauge the cybersecurity posture of an entity, enabling a more secure digital environment and aiding risk management. | Utilizing Cyber Risk Quantification standards to assess cyber risk factors and generate a score reflecting the entity’s cyber risk. | Cyber Risk Score, detailed reports, recommendations, and potential consulting services for improving cybersecurity. |
| Third-Party Risk Management (TPRM) including Supply Chain Risk Analysis | To identify, assess, and mitigate cyber risks within the supply chain, ensuring operational continuity and data protection. | Evaluating the cybersecurity posture of entities within the supply chain, considering interdependencies, and assessing potential cascading impacts. | Supply Chain Risk Analysis report, risk score, detailed findings, and recommendations for risk mitigation. |
| Shadow IT Risk Analysis | To identify assess, and mitigate security risks of identified but unauthorized IT systems, and align technological resources with organizational policies. | Rapidly assessing unmanaged IT assets, analyzing risks they pose, and evaluating organizational readiness to address Shadow IT-related risks. | Shadow IT Risk Analysis report, risk score, detailed findings, and recommendations for managing Shadow IT. |
| Insurtech Risk Analysis | To ensure secure utilization of cyber insurance solutions, promoting trust and enabling sustainable growth of cyber insurance adoption. | Examining organisations for cyber risk vulnerabilities and delivering a cyber risk posture used to assess thousands of organisations across various industries . | Insurtech Risk Analysis report, risk score, detailed findings, and recommendations for enhancing cybersecurity. |
| Cyber Security Services Organization including Resellers and Channel Partners | To provide efficient, cost-effective, and scalable cybersecurity assessment solutions. | Integrating automated Cyber Risk Assessments and Vulnerability Scans, alongside manual penetration testing for more complex or sensitive environments. | Automated Cyber Risk Assessments, Vulnerability Scans, manual penetration testing services, and detailed reports. |
This table encapsulates the Why, How, and What for six different use cases based on the Golden Circle model.