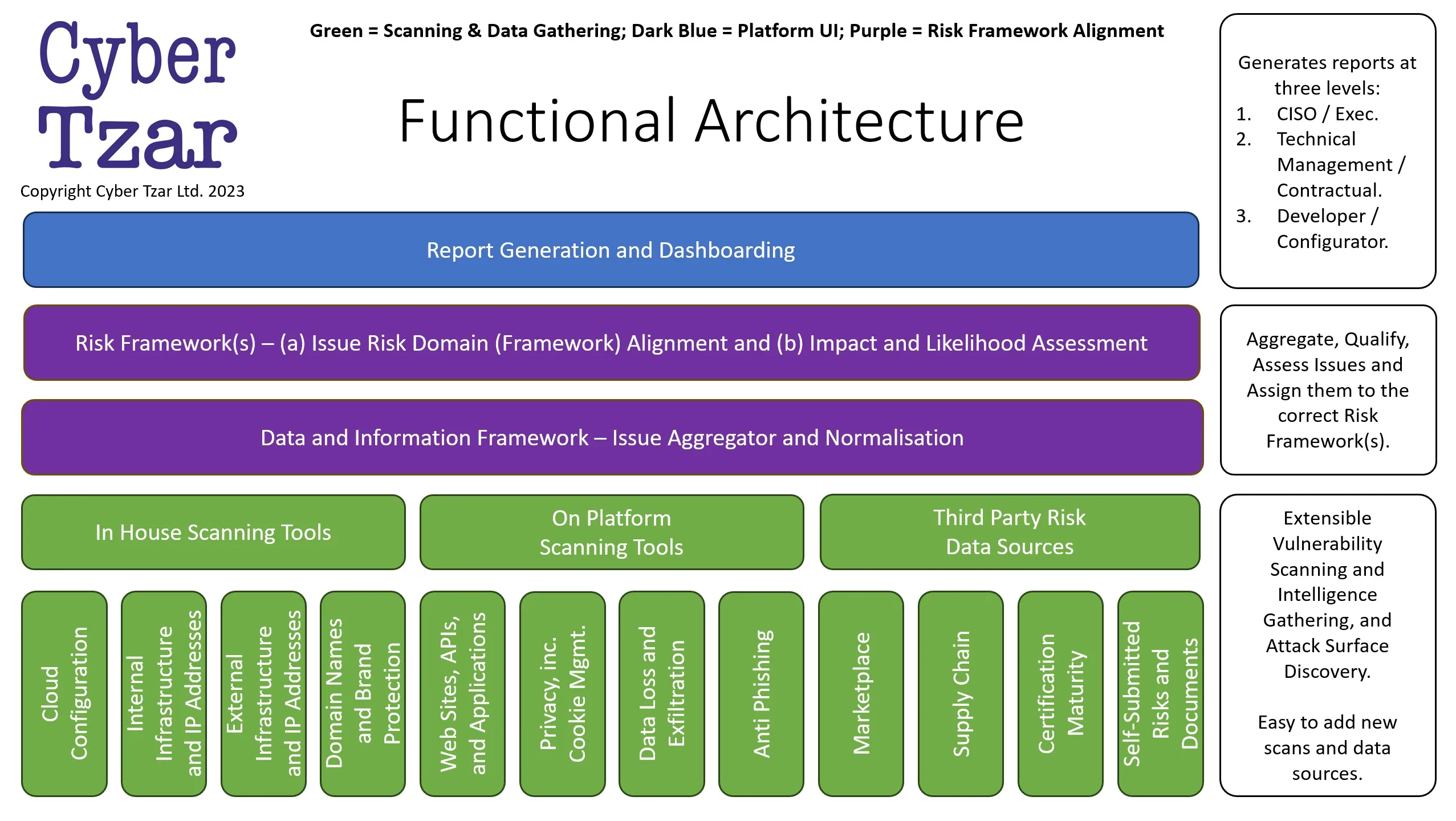
Cyber Tzar Functional Architecture
If you’re interested in how the Cyber Tzar Cyber Risk Management platform “works” you’ve come to the right place.
Here’s an overview of the Cyber Tzar Functional Architecture.
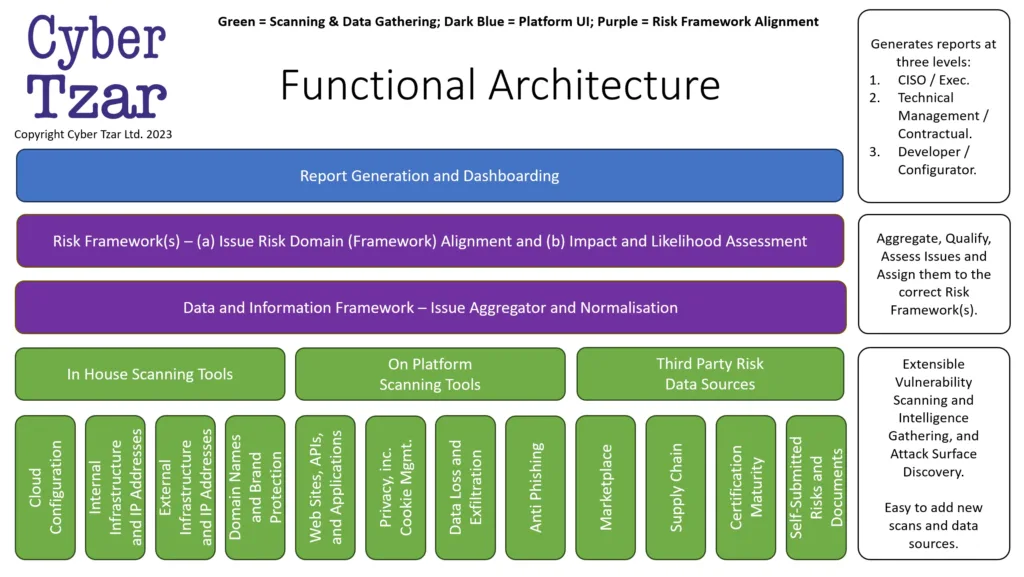
Cyber Tzar Functional Architecture
Overview
The designed functional architecture seamlessly integrates different scanning tool tiers into a unified framework. It emphasizes Extensible Vulnerability Scanning and Intelligence Gathering with a focus on Attack Surface Discovery. What sets this architecture apart is its modularity. Not only does it efficiently Aggregate, Qualify, and Assess Issues, but it also ensures they’re assigned to the correct Risk Framework(s). Furthermore, the system’s design ensures it’s easy to add new scans and data sources, making it future-proof and adaptable to evolving cyber landscapes.
Architectural Layers
Report Generation and Dashboarding
This layer stands as the system’s front end for visualization. It’s designed to serve multiple audience types, namely:
- CISO / Exec: Tailored for top-level strategic decision-making, these reports provide summaries, trend analyses, and highlight critical risks. They are meant for those who need a bird’s eye view of the organization’s security posture.
- Technical Management / Contractual: Geared towards individuals who manage the technical and contractual aspects of the system. This includes the performance of various scanning tools, service agreements, and SLAs with third-party data sources.
- Developer / Configurator: This level of reporting is technical in nature. It details vulnerabilities, misconfigurations, and issues that need patching or remediation at the code or system level.
Risk Framework(s)
This layer aids in the classification and prioritization of issues.
- Issue Risk Domain (Framework) Alignment: Every detected issue is mapped to a specific domain within the risk framework, ensuring that each issue is addressed by domain experts.
- Impact and Likelihood Assessment: Here, every risk is quantified based on its potential impact and the likelihood of it being exploited. This quantification helps in risk prioritization.
Data and Information Framework – Issue Aggregator and Normalisation
Data from various sources, whether internal or external, gets fed into the aggregator. This aggregator not only compiles the data but also normalizes it to maintain a consistent format, facilitating a more straightforward analysis.
Combined Scanning and Data Gathering Layer
- In-House Scanning Tools: These are proprietary tools developed in-house, specifically tailored to the organization’s unique infrastructure and requirements.
- On-Platform Scanning Tools: These tools, while not built in-house, are hosted on the organization’s platform and provide more general scans compared to the bespoke in-house tools.
- Third-Party Risk Data Sources: External vendors or platforms provide these data sources, offering valuable insights into broader, industry-wide threats and vulnerabilities.
Scanning Tool Tiers (under Combined Layer)
This layer presents a suite of scanning tools, each catering to specific areas of the cyber landscape:
- Internal Infrastructure, and IP Addresses: Scan and monitor the internal network, ensuring all devices are secure.
- Self-Submitted Risks and Documents: Allows stakeholders to submit potential risks or relevant documents for assessment.
- Cloud Configuration: Assesses the security configuration of cloud services.
- External Infrastructure and IP Addresses: Monitors the organization’s external-facing infrastructure for vulnerabilities.
- Domain Names and Brand Protection: Ensures the organization’s brand isn’t misused or impersonated online.
- Websites, APIs, and Applications: Scans for vulnerabilities or misconfigurations in web applications and related interfaces.
- Privacy, inc. Cookie Mgmt.: Ensures compliance with privacy regulations and proper management of cookies on websites.
- Data Loss and Exfiltration: Monitors for potential data breaches or unauthorized data transfers.
- Anti Phishing: Scans for potential phishing threats targeting the organization.
- Marketplace: Assesses risks related to online marketplaces the organization might utilize.
- Supply Chain: Ensures the security integrity of the organization’s entire supply chain.
- Certification Maturity: Assesses and tracks the maturity level of various certifications the organization holds or seeks.
The current “hot” topic in IT and Cyber is AI and we use AI in multiple ways at this layer, including:
- Dynamic testing to create unique attacks in the process of using the application being tested.
- Speculative searches of exfiltrated data based on email addresses.
- Tests for brand sitting and phishing web site testing, in terms of comparative analysis of site aspects.
What is a “Functional Architecture”?
A functional architecture is a design blueprint that focuses on the functional aspects of a system, breaking it down into functional elements and defining the relationships between them. It primarily centers on how a system or solution achieves its functionality, rather than concentrating on system components or technology.
The purpose of this kind of architecture is to ensure that the system will fulfil its intended functional requirements. It involves organizing functionalities into separate concerns and defining the interactions between those concerns in a way that ensures they collectively satisfy the system’s functional requirements.
In summary, it’s a high-level representation of the system’s functional organization and interaction, which can be critical for understanding and constructing complex systems.